Understanding how medical data moves helps inform a robust cybersecurity process. Data is vulnerable at different points, so tracking where it goes, why, and how helps ensure data stays protected. This blog discusses why Digital Therapeutics (DTx) companies need to consider data flow for their cybersecurity strategy and gives concrete steps to ensure data isn’t compromised.
For more on why cybersecurity matters for DTx, see “Digital Therapeutic Cybersecurity: Keeping Participant Data Safe.”
Imagine you have created successful wellness apps and are beginning to move into the DTx space. Among the many questions that pop up are the types of data your new DTx will produce, where vulnerabilities exist within the data flow, and how you can be a good steward of patient data in compliance with regulations.
Data classification matters
What makes the data collected through DTx products different from data collected through wellness apps? The type of data DTx produce often falls under more stringent protections, with violators facing serious consequences. Data privacy laws vary by jurisdiction but typically include the following:
- Protection for sensitive patient data, such as personally identifiable information and health records.
- Penalties for failing to protect data.
United States: HIPAA & 21 CFR Part 11
Because DTx products produce data related to a user’s health status, the data becomes identifiable as protected health information (PHI) under the United States (US) Health Insurance Portability and Accountability Act (HIPAA). PHI is individually-identifiable health status information used to provide healthcare, healthcare payment, or healthcare operations. For example, patients’ names, medical diagnoses, and even full-face photographs fall under PHI.
If DTx fail to protect PHI, they can face government fines or prosecution.i That’s why it is essential to identify whether your DTx will be capturing PHI and ensure robust security measures are in place. Cybersecurity is also crucial for DTx to gain clearance or approval from regulatory bodies, such as the US Food and Drug Administration (FDA), on the path to commercializing their products and gaining physician, payer, and public trust.
The US also regulates electronic records, which hold the PHI generated by DTx products. The FDA’s Code of Federal Regulations (CFR) requires validation testing for software and technological solutions that create, modify, maintain, or transmit electronic records. 21 CFR Part 11 includes many other safety measures DTx must consider when handling electronic records, such as keeping records for FDA inspection, periodic authority checks, and training for personnel who work with electronic records.
European Union: GDPR
The European Union (EU)’s General Data Protection Regulation (GDPR) protects patients’ personally identifiable information, including biometric data (collected by some DTx). Unlike the FDA, the GDPR imposes regulations on organizations outside of the EU if they violate data privacy for people in the EU. Penalties for violators include significant fines—up to €20 million ($23million, £17million) or 4% of global revenue (whichever is higher).
United Kingdom: DPA 2018, UK GDPR
Patient data privacy in the United Kingdom (UK) falls under the Data Protection Act (DPA) 2018 and the UK GDPR. The DPA 2018 is a framework for data protection and supplements the UK GDPR. Data containing sensitive information, such as demographics, health, and biometrics, have legal protection under the DPA 2018.
Data flow
In September 2021, Castor interviewed Frank Falcione, Senior Executive Quality and Risk Management Consultant with Clinical Research Strategies, LLC, about cybersecurity and DTx. When asked about the risks presented by personal devices, Falcione said:
“Any app you have on your phone is an area of vulnerability. […] Anything that’s a conduit for personal information is at risk because that personal information gives people avenues to other mechanisms to get into other systems.”
In other words, open and unprotected channels can allow malicious parties to access and use patient data. Data is particularly vulnerable as it moves, which is why understanding data flow matters so much to DTx. App-generated data is more likely than traditional electronic medical records (EMR) to be compromised in transit.
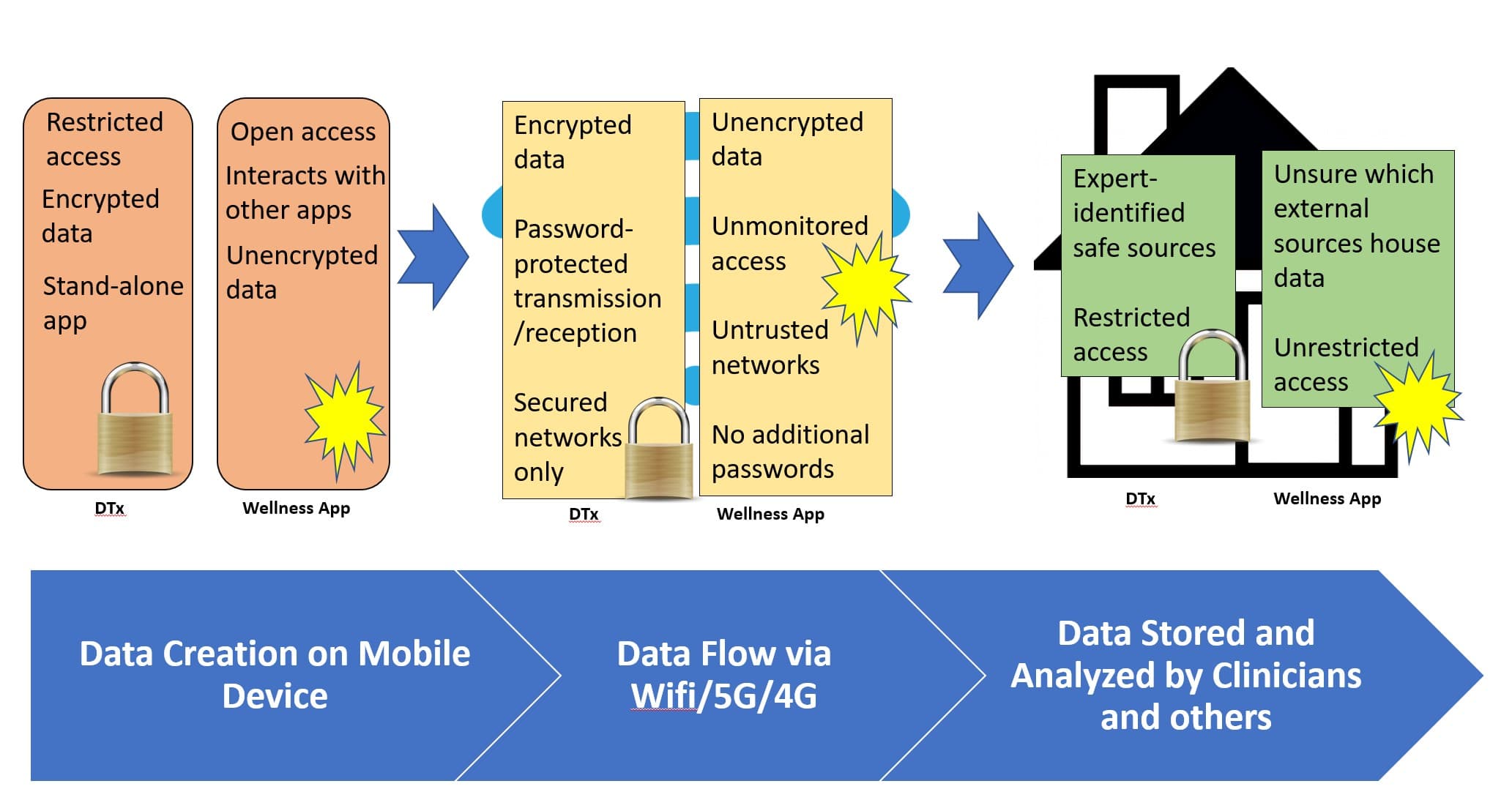
When using an app on a personal device, data can flow from the device through conduits like internet networks into external software or storage spaces (such as the cloud or a database). DTx must protect sensitive data during each stage of the flow. Table 1 shows the differences between unprotected data (characterized by wellness apps) and protected data (DTx) during each step of the data flow journey.
Table 1. Unprotected vs. Protected Data Flow
Step |
Data Flow Description |
Unprotected Data(Wellness apps) |
Protected Data (DTx) |
| 1. | Apps on personal devices collect and store data. |
|
|
| 2. | Data moves through conduits to other locations where it is stored and analyzed. |
|
|
| 3. | Data lands in sources that house data. |
|
|
Data stewardship
Let’s go back to the initial scenario. You’re transitioning from developing wellness apps to a DTx series. You understand that you will now have to think about cybersecurity to protect sensitive patient data and abide by regulatory body requirements. What steps can you take to be a good steward of patient data?
- Do a data inventory: Identify the information your DTx collects that will need to be protected.
- Track your data: Determine how data is retained in your app and transported out of your app. Where does the data reside? How is it transmitted?
- Protect your data: Apply protective measures such as data encryption and password protection. Eliminate potential breaches, such as disabling Locations or Camera if they are not needed.
Establishing a robust cybersecurity system is greatly helped by a security expert with a track record of guiding DTx development. Larger companies may have the infrastructure to support this, whereas startups may need a responsible third party to complete the task.
Whether you’re transitioning your wellness app to a DTx or have an established DTx product line, robust cybersecurity measures are integral to a successful product. Securing data flow and protecting users’ sensitive information helps meet regulatory requirements and maintain public trust.